Recently I got myself a GPS module to play with such as this. Not that I knew much about but felt like something nice to play with. First thing first is connecting the GPS module to the GPIO in Orange Pi 2G. In my case I decided to connect the GPS to ttyS2, asides from VCC (2.8V) and GND. This correspond to pins 1, 6, 8 and 10.
Vcc -> pin 1
GND -> pin 6
TxD -> pin 8
RxD -> pin 10
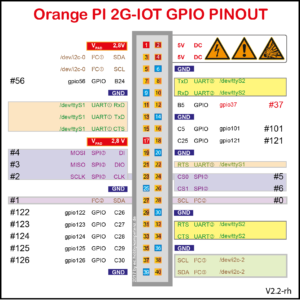
Pin 1 would be the one just below a small white arrow to the left of the SD card. Below two pictures of GPS connected to Orange Pi GPIO pins.
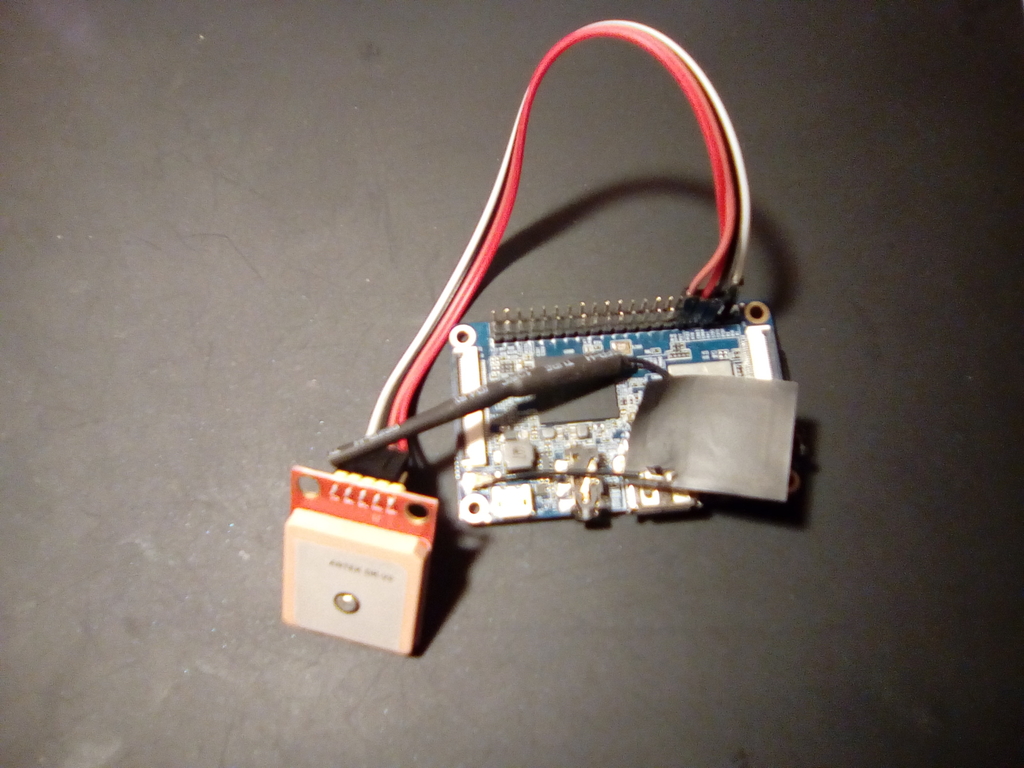

Another important thing is to cross TxD and RxD cables, that means connecting GPS TxD to Orange Pi RxD and GPS RxD to Orange Pi TxD.
Now that the GPS module is connected to the Orange Pi power it up and log into it. We will now check if the GPS mocule is working, in order to do this we will connect via minicom.
minicom -D /dev/ttyS2 -b 9600 Welcome to minicom 2.7 OPTIONS: I18n Compiled on Apr 26 2017, 00:45:18. Port /dev/ttyS2, 19:10:00 Press CTRL-A Z for help on special keys $GPRMC,191013.00,A,4252.31265,N,7833.00897,W,0.180,,040518,,,A*64 $GPVTG,,T,,M,0.180,N,0.333,K,A*29 $GPGGA,191013.00,4252.31265,N,7833.00897,W,1,06,2.16,296.4,M,51.3,M,,*44 $GPGSA,A,3,22,16,10,08,26,27,,,,,,,3.81,2.16,3.14*04 $GPGSV,3,1,10,01,19,244,,08,60,313,24,10,49,079,28,16,36,164,36*74 $GPGSV,3,2,10,18,42,250,22,20,07,038,,21,06,061,,22,09,195,30*7A $GPGSV,3,3,10,26,09,158,30,27,69,072,27*70 $GPGLL,4252.31265,N,7833.7897,W,191013.00,A,A*7C